“scammers are now including the ‘genuine’ part of a web site within their scam email links. “
Take extra care when checking outbound links in emails.
This article explains just one small way to show how scam emails are being more sophisticated, and what you can do to spot them.
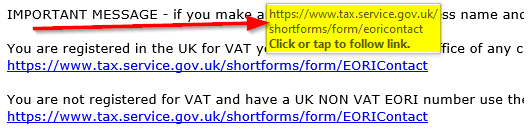
Historically you could easily identify a scam email by hovering your mouse over any buttons or links in the email. For example, if you get an email from HMRC (like the one shown below which is genuine) you would expect the the link to say tax.service.gov.uk or similar:
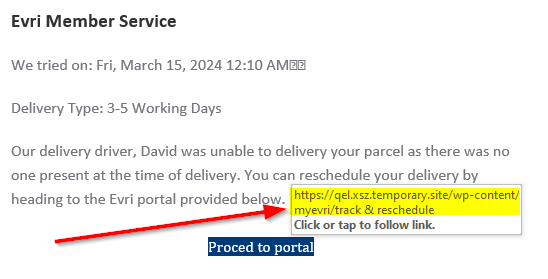
The less sophisticated scams will not have links like this. They will typically redirect you to some weird or random URL as shown in this parcel scam email below. You can see the link is not sending you to the “Evri” website but is – if you click on the link – going to send you to some random “temporary.site” – nothing to do with Evri at all!
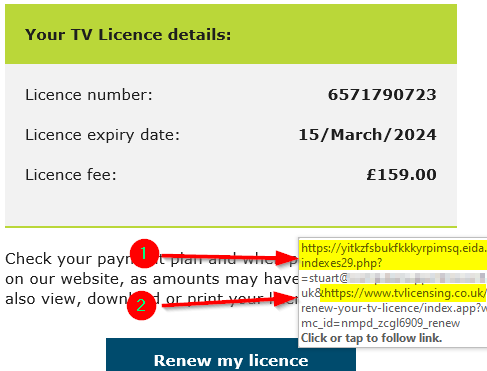
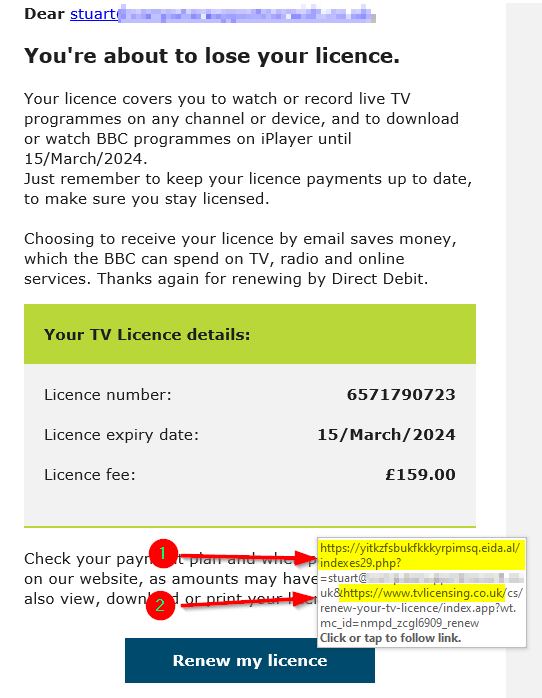
The point I wish to make today is that scammers are now including the “genuine” part of a web site within their scam email links. In this example (1) you will end up at a website ending “eida.al” but the genuine link to tvlicencing.co.uk has been included (2) to throw you off the scent. This is not a new technique, but it is now being more commonly used.
So – the advice is to be extra careful, If you think an email might be a scam, it probably is. Checking outbound links on emails is one way to verify if an email is genuine, but you need to take extra care when you do so. Just because you see a link to a genuine web site in an email it does not mean that link is genuine!
To help your organisation avoid these problems, ensure that you have….
- An email scanning tool in place that will try to identify these threats before they reach your users inbox.
- A proper training and user education plan to help users spot these threats.
- Web protection tools that will block these threats if they do get through and are clicked on.
If your email service provider is not filtering these out, or your IT provider is not offering user training or web protection tools to protect your network, you might want to rethink your email security and user training strategy.
